Table of Contents
- Sftp Using Public Key
- Get Ssh Public Key
- Ssh Using Private Key File
- Ssh Public And Private Keys
- Ssh Using Public Key File
- Ssh Using Public Key Command Line Ubuntu
- Append the public key (id rdsa.pub) for your source machine (where you're sshing from) to the /.ssh/authorizedkeys file of the destination server for the username you want to ssh into. If you've lost the public key, you'll want to create a new one with ssh-keygen. Using the default arguments for that should be ok for most purposes.
- SSH to Linux using Public KeyHelpful? Please support me on Patreon: thanks & praise to God, and with thanks to the.
Anyone (or any device) that has the public key is able to encrypt data that can only be decrypted by the private key. This means you can share the public key with anyone you want, and they will be able to send you encrypted messages. The private key has to be protected make sure it doesn’t leave your computer. I know that private key authentication works, however I'm looking for public key authentication. I'm trying to establish a connection using SSH.NET and a public key. In the Git Bash terminal I can connect and run commands fine using my public key, but when I try connecting to the same host using SSH.NET I.
Introduction
SSH can handle authentication using a traditional username and password combination or by using a public and private key pair. The SSH key pair establishes trust between the client and server, thereby removing the need for a password during authentication. While not required, the SSH private key can be encrypted with a passphrase for added security.
The PuTTY SSH client for Microsoft Windows does not share the same key format as the OpenSSH client. Therefore, it is necessary to create a new SSH public and private key using the PuTTYgen tool or convert an existing OpenSSH private key.

Requirements
- PuTTY SSH client for Microsoft Windows
- Remote server accessible over OpenSSH
Install PuTTY and PuTTYgen
Both PuTTY and PuTTYgen are required to convert OpenSSH keys and to connect to the server over SSH. These two tools can be downloaded individually or, preferably, as a Windows installer from the PuTTY Download Page.
Once the PuTTY Windows installer is downloaded, double-click the executable in the Download folder and follow the installation wizard. The default settings are suitable for most installations. Both PuTTY and PuTTYgen should now be accessible from the Windows Programs list.
Use Existing Public and Private Keys
If you have an existing OpenSSH public and private key, copy the id_rsa key to your Windows desktop. This can be done by copying and pasting the contents of the file or using an SCP client such as PSCP which is supplied with the PuTTY install or FileZilla.
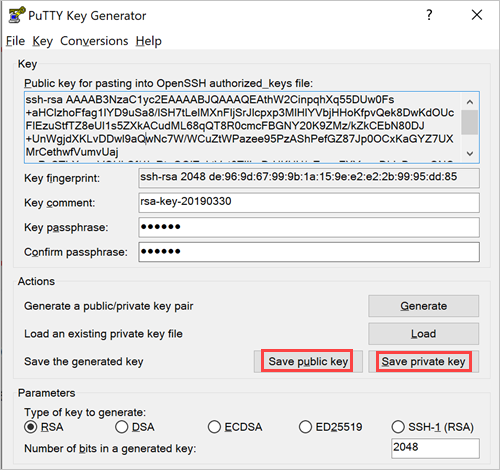
Next launch PuTTYgen from the Windows Programs list.
- Click
Conversionsfrom the PuTTY Key Generator menu and selectImport key. - Navigate to the OpenSSH private key and click
Open. - Under
Actions/Save the generated key, selectSave private key. - Choose an optional passphrase to protect the private key.
- Save the private key to the desktop as
id_rsa.ppk.
If the public key is already appended to the authorized_keys file on the remote SSH server, then proceed to Connect to Server with Private Key.
Otherwise, proceed to Copy Public Key to Server.
Create New Public and Private Keys
Launch PuTTYgen from the Windows Programs list and proceed with the following steps.
- Under
Parameters, increase theNumber of bits in a generated key:to a minimum value of 2048. - Under
Actions/Generate a public/private key pair, clickGenerate. - You will be instructed to move the mouse cursor around within the PuTTY Key Generator window as a randomizer to generate the private key.
- Once the key information appears, click
Save private keyunderActions/Save the generated key. - Save the private key to the desktop as
id_rsa.ppk. - The box under
Key/Public key for pasting into OpenSSH authorized_keys file:contains the public key.
Copy Public Key to Server
The OpenSSH public key is located in the box under Key / Public key for pasting info OpenSSH authorized_keys file:. The public key begins with ssh-rsa followed by a string of characters.
- Highlight entire public key within the PuTTY Key Generator and copy the text.
- Launch PuTTY and log into the remote server with your existing user credentials.
Use your preferred text editor to create and/or open the
authorized_keysfile:Paste the public key into the
authorized_keysfile.Save the file and close the text editor.
Adjust the permissions of the
authorized_keysfile so that the file does not allow group writable permissions.Logout of the remote server.
Connect to Server with Private Key
Now it is time to test SSH key authentication. The PuTTYgen tool can be closed and PuTTY launched again.
- Enter the remote server Host Name or IP address under
Session. - Navigate to
Connection>SSH>Auth. - Click
Browse...underAuthentication parameters/Private key file for authentication. - Locate the
id_rsa.ppkprivate key and clickOpen. - Finally, click
Openagain to log into the remote server with key pair authentication.
Overview
Public key authentication is a way of logging into an SSH/SFTP account using a cryptographic key rather than a password.
If you use very strong SSH/SFTP passwords, your accounts are already safe from brute force attacks. However, using public key authentication provides many benefits when working with multiple developers. For example, with SSH keys you can
- allow multiple developers to log in as the same system user without having to share a single password between them;
- revoke a single developer's access without revoking access by other developers; and
- make it easier for a single developer to log in to many accounts without needing to manage many different passwords.
How Public Key Authentication Works
Keys come in pairs of a public key and a private key. Each key pair is unique, and the two keys work together.
These two keys have a very special and beautiful mathematical property: if you have the private key, you can prove you have it without showing what it is. It's like proving you know a password without having to show someone the password.
Public key authentication works like this:
- Generate a key pair.
- Give someone (or a server) the public key.
- Later, anytime you want to authenticate, the person (or the server) asks you to prove you have the private key that corresponds to the public key.
- You prove you have the private key.
You don't have to do the math or implement the key exchange yourself. The SSH server and client programs take care of this for you.
Generate an SSH Key Pair
You should generate your key pair on your laptop, not on your server. All Mac and Linux systems include a command called ssh-keygen that will generate a new key pair.
If you're using Windows, you can generate the keys on your server. Just remember to copy your keys to your laptop and delete your private key from the server after you've generated it.
To generate an SSH key pair, run the command ssh-keygen.
It will look like this when you run it:
You'll be prompted to choose the location to store the keys. The default location is good unless you already have a key. Press Enter to choose the default location.
Next, you'll be asked to choose a password. Using a password means a password will be required to use the private key. It's a good idea to use a password on your private key.
After you choose a password, your public and private keys will be generated. There will be two different files. The one named id_rsa is your private key. The one named id_rsa.pub is your public key.
You'll also be shown a fingerprint and 'visual fingerprint' of your key. You do not need to save these.
Configure an SSH/SFTP User for Your Key
Method 1: Using ssh-copy-id
Now that you have an SSH key pair, you're ready to configure your app's system user so you can SSH or SFTP in using your private key.
Sftp Using Public Key
To copy your public key to your server, run the following command. Be sure to replace 'x.x.x.x' with your server's IP address and SYSUSER with the name of the the system user your app belongs to.
Method 2: Manual Configuration
If you don't have the ssh-copy-id command (for example, if you are using Windows), you can instead SSH in to your server and manually create the .ssh/authorized_keys file so it contains your public key.
First, run the following commands to make create the file with the correct permissions.
Get Ssh Public Key
Next, edit the file .ssh/authorized_keys using your preferred editor. Copy and paste your id_rsa.pub file into the file.
Log In Using Your Private Key
You can now SSH or SFTP into your server using your private key. From the command line, you can use:
If you didn't create your key in the default location, you'll need to specify the location:
If you're using a Windows SSH client, such as PuTTy, look in the configuration settings to specify the path to your private key.
Granting Access to Multiple Keys
The .ssh/authorized_keys file you created above uses a very simple format: it can contain many keys as long as you put one key on each line in the file.
If you have multiple keys (for example, one on each of your laptops) or multiple developers you need to grant access to, just follow the same instructions above using ssh-copy-id or manually editing the file to paste in additional keys, one on each line.
When you're done, the .ssh/authorized_keys file will look something like this (don't copy this, use your own public keys):
Additional Information
Retrieve Your Public Key from Your Private Key
The following command will retrieve the public key from a private key:
Ssh Using Private Key File
This can be useful, for example, if your server provider generated your SSH key for you and you were only able to download the private key portion of the key pair.
Ssh Public And Private Keys
Note that you cannot retrieve the private key if you only have the public key.
Correcting Permissions on the .ssh Directory
The instructions in this article will create your server's .ssh directory and .ssh/authorized_keys file with the correct permissions. However, if you've created them yourself and need to fix permissions, you can run the following commands on your server while SSH'd in as your app's system user.
Disabling Password Authentication
NOTE: When changing anything about the way SSH is accessed(ports, authentication methods, et cetera), it is very strongly recommended to leave an active root SSH session open until everything is working as intended. This ensures you have a way to revert changes in the event something goes wrongand logins are not working properly.
Ssh Using Public Key File
As an extra security precaution, once you have set up SSH keys, you may wish to disable password authentication entirely. This will mean no users will be able to log into SSH or SFTP without SSH keys. Anyone entering a password will receive a message like:
Or:
Disabling password authentication is an excellent way to improve server security. Please see our guide here for the steps to accomplish this goal.
Ssh Using Public Key Command Line Ubuntu
Then, test whether you're able to log in with a password by opening a new SSH or SFTP session to the server. Passwords should not be able to be used and, if everything has been done correctly, an error will be issued when someone tries to use a password. Unless this setting is changed back to allow password authentication, no users will be able to log in without an SSH key set up.
